Omega Cloud: Modeling Cybercrime Economies of Stolen Data on Telegram
A glimpse into Omega Cloud, one of many ecosystems of Telegram channels and groups illegally selling stolen information
TLDR
Currently, cybercriminals are marketing and selling access to stolen user data – called Underground Clouds of Logs (UCLs) – using networks of Telegram groups and channels.
This research study offers a glimpse into Omega Cloud, one of many ecosystems of Telegram channels and groups illegally selling stolen information, as a model for other similar cybercrime operations.
The Omega Cloud network consists of 11 channels/groups and one admin account (all somehow dedicated to promoting Omega Cloud).
Below, we break down our research methodology step by step for others to model elsewhere, as it can be applied to many kinds of Telegram networks.
Introduction
Cybercriminals are using Telegram as a means for marketing, managing, and selling their wares. Underground Clouds of Logs (UCLs) are one such offering,1 wherein vendors sell access to troves of stolen information (“logs”). UCLs are often hosted in the cloud via services such as Google Drive or Mega[dot]nz.
After examining many UCL networks, we found that UCLs are often promoted by a web of interconnected channels and chats rather than by one single channel. This approach gives cybercriminals a wider range of marketing and communication strategies and greater resilience: if one channel should be banned, the others can still remain active.
To illustrate how these UCL-selling networks tend to operate, this piece examines one such network in particular: Omega Cloud.
Selling UCL Access on Telegram
Cybercriminals have made a home on the messaging platform Telegram for years now, partly for practical reasons: Telegram has strong privacy features, can easily integrate bots to automate workflows,2 and has millions of users around the world.3 As a result of these features, Telegram holds obvious appeal to fraudsters and cybercriminals.4
Cybercriminals have been selling access to UCLs (troves of stolen information) on Telegram for years now. These UCLs are often comprised of information stolen by stealer malware,5 and customers are offered access to it with time-based subscription models (weekly, monthly, etc.).
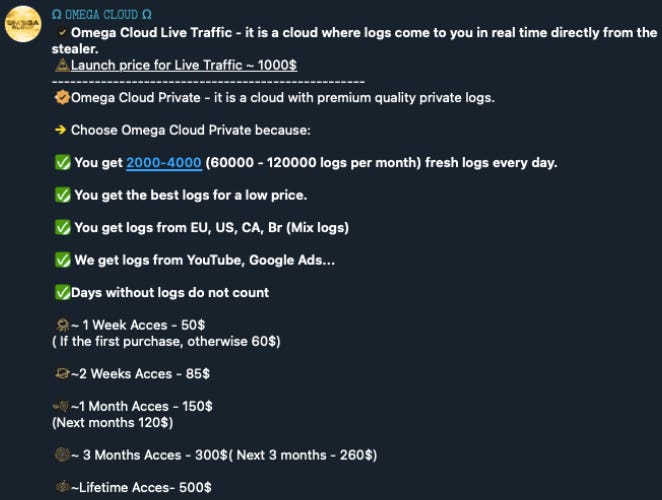
After purchasing access, customers can use the information in UCLs to commit a wide range of further crimes. The information contained in these UCLs can be used to conduct all manner of crime, though it primarily lends itself to account takeover fraud.
Through our research, we uncovered dozens of Telegram groups advertising access to UCLs. These were often easy to find, as many explicitly used the term “cloud” in their names or otherwise explicitly stated that they were selling access to stolen information.
Common Traits of UCL-Selling Networks
Many of the UCL-selling networks we studied used a wide array of Telegram’s platform features to support their businesses.
Primarily, these networks used groups (where all members can send messages and interact) and channels (where only admins can send messages to members). While many of these spaces are open to join freely, some are vetted, meaning users can only gain access through admin approval. Finally, some networks used some of Telegram’s more sophisticated features as well (eg, “boosts”), which are described in more detail further below.
To illustrate the operational similarities we found among UCL-selling networks, this piece focuses on one network in particular, Omega Cloud, to serve as a typical example.
To clarify and distinguish among Omega-related terms, in this report:
“Omega Cloud” refers broadly to the UCL-selling network and its activities.
Terms in quotations (e.g, “OMEGA CLOUD | Free Private Logs,” “Omega Chat,” “Omega free logs”) refer to specific Telegram channels and groups within Omega Cloud’s network.
Special symbols used in channel names, such as Ω (omega), have been omitted from channel titles in the written portion of this report.
Omega Cloud Background
According to Omega Cloud’s own explicit statements, the network has previously used the info-stealing malwares Meta and Redline to capture data from victims in many countries. This information comes from Telegram messages the network sent members in 2023. As of the time of writing, it is unclear what malware families Omega be using.
Activity in the “OMEGA CLOUD” Telegram channel began in Nov. 2022. Today, the channel is still active with over 9,000 subscribers, highlighting the longevity that criminal enterprises can enjoy on Telegram.
Omega Cloud on Telegram
From our preliminary research, we found that Omega Cloud’s Telegram ecosystem consists of groups and channels with widely varying activity levels.
One example of an active channel is “OMEGA CLOUD,” which is repeatedly referred to as the network’s main channel. “OMEGA CLOUD” posts multiple messages a week.
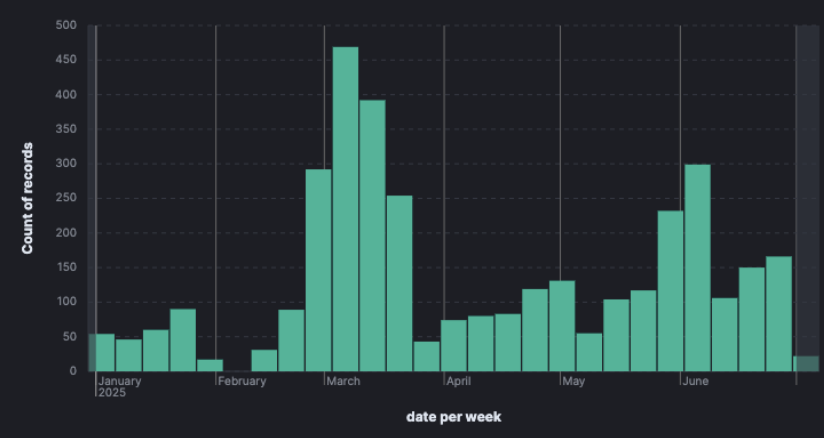
In contrast, we also found many groups and channels containing very few or no messages that seemingly served as landing pages, with the purpose of directing interested parties to a subsequent channel.
To illustrate, the “Omega Chat” group is a highly active Telegram group. In one of the many messages posted in the chat by the admin, there is a list of links to other Omega-related channels. Clicking one of the links titled “our logs” directs to another channel titled “Omega free logs.”
“Omega free logs” has only one message: a Telegram link which directs to the channel “OMEGA CLOUD | Free Private Logs”. This channel contained 14 total messages, sharing free downloadable files allegedly claiming to contain logs. We did not verify the contents of these files.
This flow is detailed in the visual below:
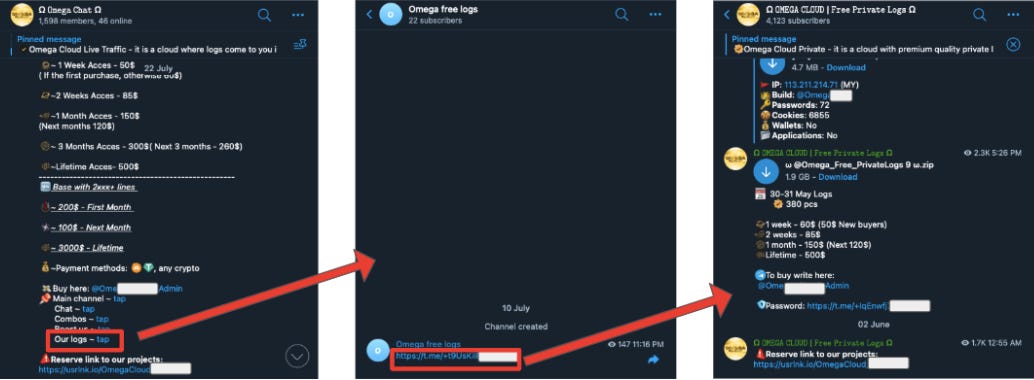
In short, some channels and groups we found contained hundreds of messages (e.g, “OMEGA CLOUD,” “Omega Chat”), some channels contained only one link (e.g., “Omega free logs”), and others fell somewhere in between (e.g, “OMEGA CLOUD | Free Private Logs,” with 14 messages).
URLs in Telegram Messages
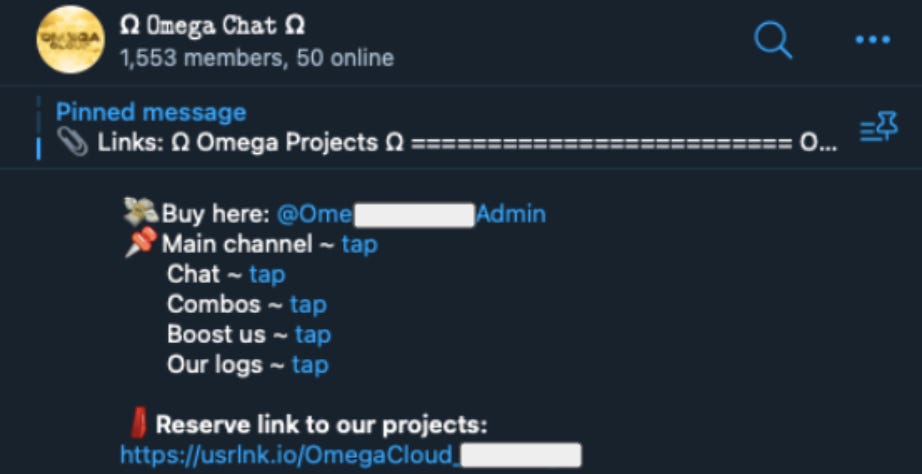
The Omega Cloud organization uses a network of Telegram channels and groups – as well as other Telegram functionality – to support their enterprise. These Telegram outlets often share links to other channels and groups (illustrated by the image below). We were interested in learning more about this interconnectedness by using Open Measures’ Telegram data to scale our analysis.
Using Open Measures Telegram Data
Open Measures’ Telegram data includes collections of messages from Telegram channels and groups of interest. These messages are indexed and their data parsed into dozens of fields (for example, the time a message was sent, the number of times a message was forwarded, etc.) For our investigation, we were interested in the data field entities.url. This field shows us a list of URLs contained in messages.
From what we’ve seen of the Omega Cloud network so far, we know that they regularly post messages that contain links to their other Telegram outlets. We therefore anticipate that this field will show us a myriad of groups and channels in support of the Omega Cloud enterprise (with an example shown in the image below).
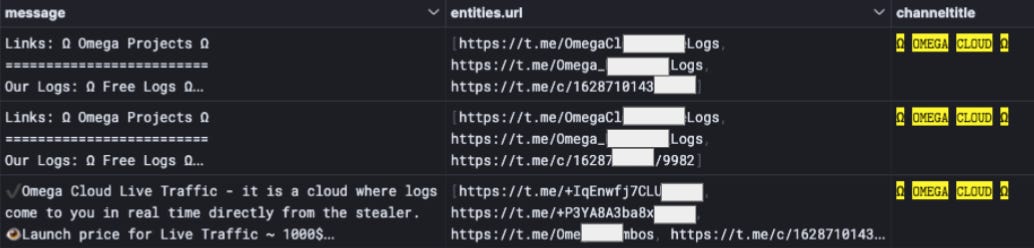
With these URLs, we can learn more about how various channels are connected to one another, as we’ll outline below.
Link Analysis
To start our investigation, we knew that we had found some of the channels and groups affiliated with Omega Cloud. Some of these groups were easy to find and very visible on Telegram.
From our preliminary investigation poking around these channels, we knew that there were likely other groups and channels – of varying levels of activity – connected to them. Instead of manually discovering and mapping out channels, we chose to use the information we already had within the Open Measures Telegram dataset to do the heavy lifting of exposing this network.
Our preliminary investigation identified only two channels/groups within the Omega Cloud ecosystem that post multiple times a week: “OMEGA CLOUD” and “Omega Chat.” The rest are significantly less active. For this reason, we will start our investigation by focusing on these two channels, as they generate a lot of content.
Data and Methodology
Using Open Measures Telegram data, we queried all messages sent by these two outlets from July 1–7, 2025. We picked this narrow date range as many messages in both the “Omega Chat” and “OMEGA CLOUD” outlets were often repetitive, and contained the same links to other Telegram channels and groups. From this, we assessed that a wider date range was not necessary, as it would give us this same data.
We then downloaded a CSV containing information from all the messages sent in the “OMEGA CLOUD” Telegram channel during the first week of July 2025. We were not interested in the messages themselves, but rather the URLs mentioned in the messages, which appear in the field entities.url. We structured our CSV as follows:
Column A: contains the date field. This is not necessary for our investigation, but is a reminder that this information came from the first week of July 2025.
Column B: this is where the Telegram group or channel’s name appears, as the channeltitle field.
Column C, D, etc.: these columns are for our entities.url results.
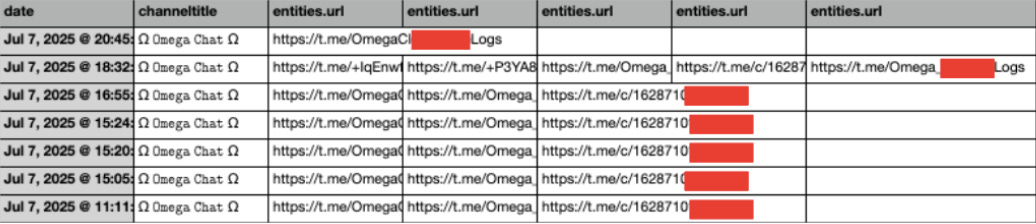
Likewise, we also downloaded a CSV of relevant information from “Omega Chat.”
Graphing the Network
We wanted to explore the connections between these groups, and to use that information as a backbone to continue building out connections. There are a number of link analysis tools available to do, but for this investigation, we used Maltego, a link analysis tool with a free Community Edition.
We imported the aforementioned CSVs (one from “Omega Chat,” another from “OMEGA CLOUD”) into Maltego. After a little bit of data clean-up (e.g., standardizing URLs and channel names), we got the following graph:
Using the entities.url field, we extracted new URLs from messages. This surfaced four other Telegram groups and channels connected to the Omega Cloud network. We also found mentions of the URL to the the “Boost” feature (discussed later in this report) for “OMEGA CLOUD.” The image above also clearly shows interconnections between “Omega Chat” and “OMEGA CLOUD,” used to begin the investigation.
Developing the Network
With the groundwork established above, we manually inspected each Telegram outlet to explore its connections to others. Since most outlets had few total messages, we did this manually rather than export data.
After completing this step, we got the following graph:
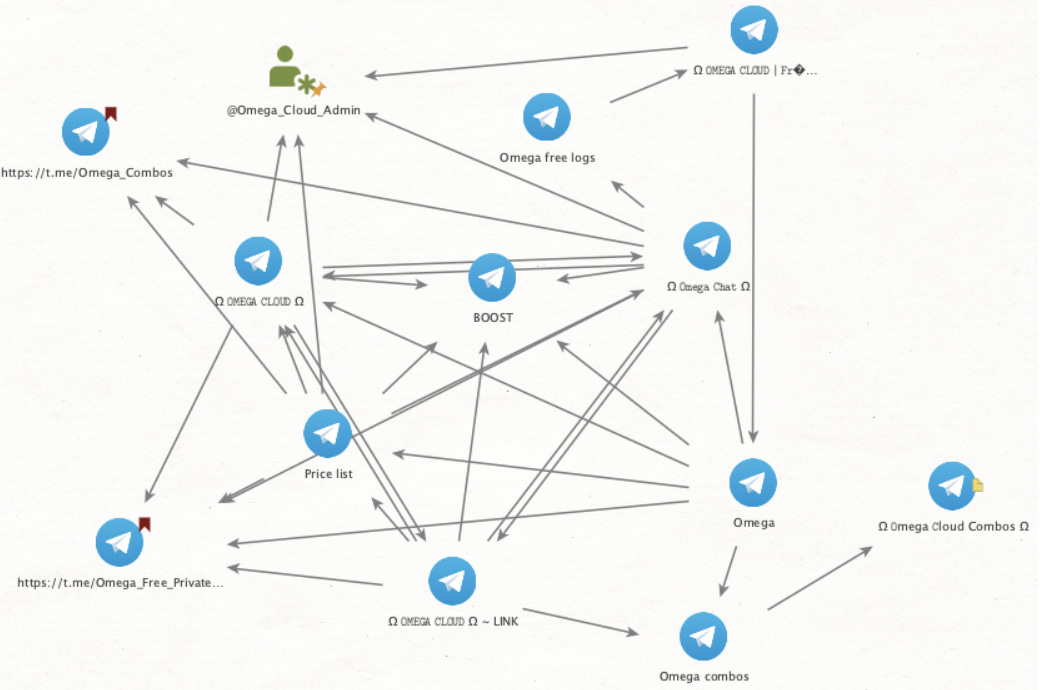
What emerged was a dense, interconnected web of Telegram channels and groups. We found a total of 11 groups/channels and one admin account. Additionally, the groups repeatedly shared a link to “boost” the main “OMEGA CLOUD” channel.
Note that the two Telegram entities above with red flags are defunct channels. Though we found links to the channels, they no longer existed. Further, we found one Telegram outlet, “Omega Cloud Combos,” that required vetting to join. As a result, we were unable to uncover additional connections related to this channel.
Omega Cloud Network Analysis
With our network mapped, we can examine each of the channels and groups in more detail. Below is a quick overview of some of the primary groups and channels, along with other information we found:
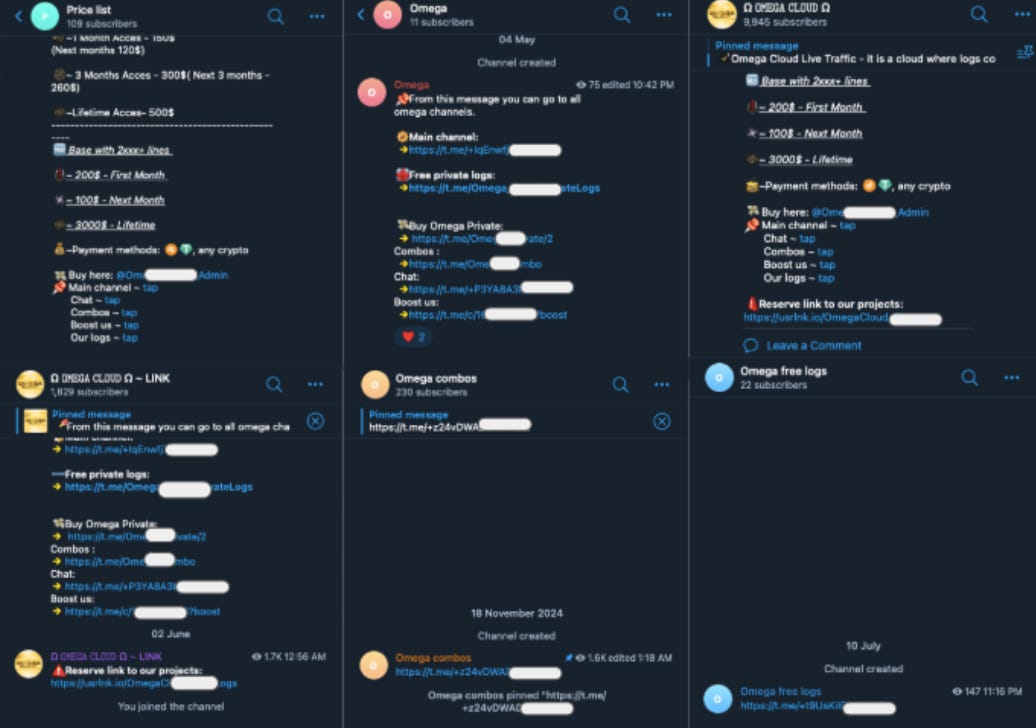
OMEGA CLOUD:
The main Telegram channel promoting Omega Cloud, with information about pricing and services. This channel is very active, with admins posting information promoting Omega Cloud’s services. It also contains downloadable free “logs” (stolen information). The naming of some of these downloadable files suggest that they may be sourced from other, rival UCL providers.
Omega Chat:
A Telegram group where Omega Cloud enthusiasts can interact with each other. Many messages in “Omega Chat” are individuals asking for advice (“is there a way to get free vbv cards?”). Others concern buying or selling criminal services (“If anyone need whatsapp bans dm me”), among similar criminal discussions. “Omega Chat”’s group admin posts messages advertising Omega Cloud which closely parallel messages found in the “OMEGA CLOUD” channel.
Admin:
To gain access to the Omega Cloud UCL, interested parties are directed to message a specific admin account in a one-on-one Telegram chat. It is unclear whether this account is also responsible for administering the various Telegram groups and channels.
Boosts:
Premium Telegram subscribers can give channels “boosts.” Premium Telegram subscribers may choose to "boost" a group or channel they enjoy or want to see gain greater visibility. With enough boosts, a Telegram channel can post additional stories and have more customization.6 The Omega Cloud operators regularly share the link to boost their main Telegram channel, “OMEGA CLOUD.” This underscores how these criminal operators are comfortable operating in the open on Telegram.
The remaining Telegram channels and groups we identified largely have overlapping messages and focuses. These include promoting Omega Cloud, providing links to various services, and providing free downloads of logs to catch client interest.
Conclusion
As exemplified by Omega Cloud, cybercriminal groups openly promote and sell stolen data via UCLs on Telegram. They accomplish this through interconnected networks of Telegram channels and groups, some of which are entirely public while others are private and vetted.
These cybercriminals use networked Telegram groups and channels for resilience should any of their outlets be taken offline (and also allows for specialized sub-chats). Network admins take advantage of advanced features like boost by directing their subscribers – in this case, their Premium Telegram subscribers – to give them boosts to help amplify their reach (as Omega Cloud does with its main “OMEGA CLOUD” channel).
In response to a wide range of international pressure and criticism, Telegram announced in Sept. 2024 that it would begin sharing users’ IP addresses and phone numbers with authorities for valid legal requests.7 The policy reversal was intended to demonstrate Telegram’s increased commitment to slowing cybercrime on its platform. Still, our research shows that Telegram remains popular with cybercriminals and fraudsters, as they continue to operate there with relative freedom.
In this piece, we outlined our full methodology for exploring interconnected Telegram networks. Though our focus was on UCL-selling networks, this methodology can also help researchers expose networks of violent extremists, political messaging groups, and many others.
Identify disinformation and extremism with the Open Measures platform.
Organizations use Open Measures’ tooling every day to track trends related to networks of influence, coordinated harassment campaigns, and state-backed info ops.
Group‑IB. (n.d.). Underground Cloud of Logs. Group‑IB Knowledge Hub. Retrieved July 23, 2025. Here.
Ibid.
Singh, M. (2021, Aug. 30). Telegram tops 1 billion downloads. TechCrunch. Retrieved July 23, 2025. Here.
KELA Cyber Team. (2024, Sept. 26). Telegram’s policy shift: How cybercriminals are reacting to new data‑sharing rules (B. Kapon, Ed.). KELA Cyber Blog. Retrieved July 23, 2025. Here.


